A Special Dispatch for the DAOSRUS Community
The Ultimate Trail Map: Why Your Digital Passport is Now Built on Radio Waves
RF Fingerprinting: The Un-Spoofable Security That Guarantees True Autonomy
From IP Addresses to Physical Reality: The Adventure in Identity
The Digital Adventures Outdoors R Us community is defined by a pursuit of autonomy, decentralization, and the secure mastery of new frontiers—whether that frontier is a mountain peak or the bleeding edge of the digital economy.
For years, we’ve navigated the digital world with what amounts to a flimsy paper map: the IP Address and the MAC Address. We’ve been told these are our IDs, but any seasoned digital adventurer knows these are easily forged. They are software-defined; they can be spoofed, cloned, and hijacked.
In the high-stakes, decentralized environment of systems like the RIOS Campus—where energy microgrids meet AI Compute Engines—relying on a spoofable ID is the security equivalent of leaving your basecamp unlocked in the wilderness. It’s an unacceptable risk.
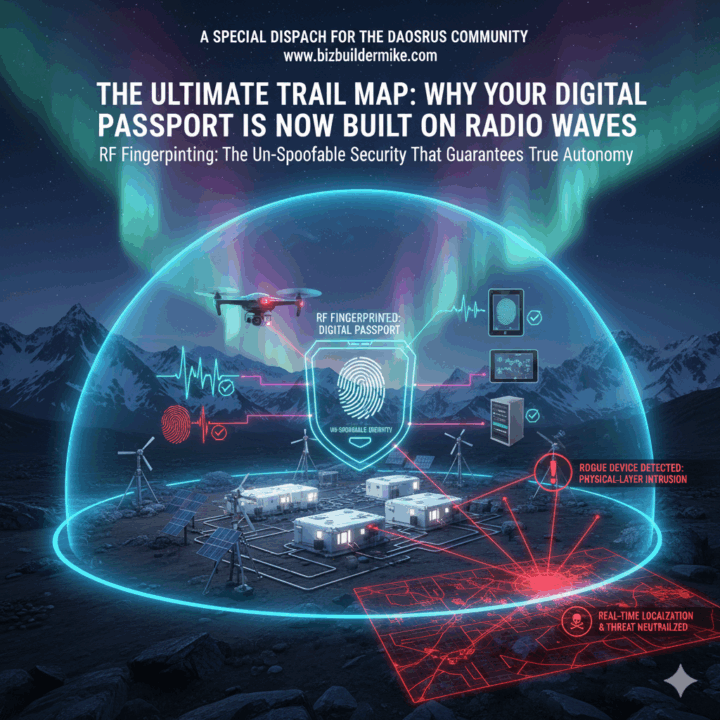
The future of security is demanding a new form of identification—a Digital Passport that is not stored on a server, but is permanently inscribed in the very fabric of the device itself. This is the revolutionary concept of Radio Frequency Fingerprinting (RFF), and it’s the most exciting development in digital autonomy you haven’t heard about yet.
Your Signal is Your Signature: The Un-Spoofable Passport
Imagine this: Every single wireless device you own—from your satellite communicator to the Wi-Fi chip in your industrial drone—is physically unique.
When a device is manufactured, no matter how precise the process, tiny, microscopic variations in the components (the capacitors, the oscillators, the filters) are unavoidable. These imperfections are subtle, but when the device transmits a radio signal, they translate into a minute, unique distortion in the signal’s wave. This is a Physical-Layer Characteristic—a kind of sonic boom of its existence.
This minute distortion is the Radio Frequency Fingerprint (RFF).
It is a signature tied not to software or a username, but to the unchangeable physics of the hardware itself.
The Role of the Cognitive Mesh
In an advanced system like the RIOS Campus, the entire network is built on what we call the Cognitive Mesh. It’s not just a set of routers; it’s a swarm of highly sensitive sensors, each equipped with Dedicated Listening Radios (DLRs).
These DLRs are specialized tools that don’t just listen for data; they listen for identity. They can analyze the fine details of the transmitted radio wave—the transient signals, the frequency drift, and the phase noise—and map that information to create an un-spoofable RFF for the device.
- The Power of Certainty: Once a device is enrolled, the system knows that only a piece of hardware with that exact physical imperfection profile can be trusted. Your digital identity is now guaranteed by the laws of physics, not a password.
Zero-Trust Access: How RFF Changes the Game
In the world of DAOs and high-autonomy ventures, the principle of Zero-Trust is paramount: Never trust, always verify. RFF provides the ultimate verification layer.
1. Cloned Device Lockdown
The single most dangerous threat is a spoofed identity. A hacker can easily clone the MAC address of a trusted control unit (like a critical GTL Microgrid controller) to slip past firewalls.
- The RFF Solution: The Cognitive Mesh detects the intrusion instantly. It sees the correct MAC address, but its DLRs detect a foreign RFF. It’s a valid ID card, but the person holding it has the wrong face. The system immediately flags the device as a Physical-Layer Rogue Device, and access is denied. The digital adventure stops for the imposter.
2. Hardware-Based KYC (Know Your Customer)
In the RIOS ecosystem, security must integrate seamlessly with financial compliance (KYC/AML). RFF provides a foundational truth:
- Verifying the Asset: RFF extends KYC beyond verifying the user’s identity to verifying the integrity of the hardware they are using. This prevents bad actors from introducing un-vetted, non-compliant, or potentially malicious hardware into the financial and operational loop. Trust is established from the silicon up.
Airspace Defense: Pinpointing the Threat in Real-Time
The RFF system doesn’t just identify a threat; it provides real-time C4I (Command, Control, and Intelligence) data to neutralize it in the physical world.
The mesh network’s distributed DLRs act like a sophisticated sonic defense array. When a rogue signal is detected, the system immediately uses advanced techniques like Angle-of-Arrival (AoA) and Time Difference of Arrival (TDoA).
- Multiple Nodes Listen: Several mesh nodes simultaneously measure the subtle differences in the signal’s arrival time and direction.
- AI Triangulation: An AI engine processes the data and calculates the precise physical coordinates of the transmitter—whether it’s a rogue Wi-Fi hotspot trying to siphon data, a camera hidden in a blind spot, or a drone with a malicious payload.
This transforms a digital security alert (“Jamming detected on the 5GHz band”) into a physical, actionable response (“Rogue Jammer located at 37.7749° N, 122.4194° W – two meters from the Central Compute Engine perimeter fence”).
For the DAOSRUS community, this means true digital and physical sovereignty. It means the infrastructure powering your next great venture is protected by an invisible, un-spoofable shield that is constantly verifying the identity of everything in its airspace.
The future of security is about embracing the absolute truth of physics. It’s about leveraging advanced sensing to move from reactive defense to proactive, absolute control. This is the new digital adventure, and your un-spoofable Radio Frequency Fingerprint is your ultimate passport to its success.
